
SOC 2 vs. ISO 27001
What's the difference between SOC 2 and ISO 27001? Which is more suitable for you? ISO 27001 and SOC 2 are the two leading information security standards.
Updated: Sep-20
The two leading InfoSec assurance standards are SOC 2 & ISO 27001. What's the difference?
What’s the difference between SOC 2 and ISO 27001?
There are technical and methodology differences beyond the scope of what they cover. Perhaps more importantly, there’s varying perceptions and preferences that play a role in their adoption and use in practice.
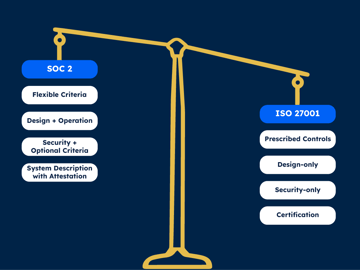
The key differences are:
1. Flexible vs. Prescribed Requirements
SOC 2 has a set of criteria that are flexible to adapt to the nature of the company, systems and services. That makes it a common choice for SaaS providers with outsourced cloud infrastructure. ISO 27001 has eight mandatory requirements, and 93 (ISO 27001:2022), previously 114 (ISO 27001:2015) predefined control activities, that are considered for all organisations. These need to be justified if they are not applied. The general feedback is this approach puts more focus on policies, procedures, and general documentation that adds more business burden. SOC 2 can be anywhere from 70 to 150 controls, with those controls defined based on what's most relevant and how they actually apply in practice.
2. Design and Operation of Controls
ISO 27001 is a standard for design and implementation of an information security management system (ISMS). SOC 2 places more focus on how security principles and operationalised to address the relevant risks. These risks are considered with respect to the services provided to customers. More regulated enterprise customers like in Financial Services and Healthcare, generally view SOC 2 as providing a higher level of assurance from this risk-based, operational focus. Operating effectiveness has become a key consideration with standards like CPS 234, and Consumer Data Right, where ISO 27001 has been deemed inadequate.
3. Security + Additional Criteria
ISO 27001 is purely an information security focus, with separate ISO standards that cover privacy, business continuity and other areas. SOC 2 has optional additional criteria for Availability, Confidentiality, Privacy and Processing Integrity, that can be included in the SOC 2 report to meet broader end-user requirements. The flexibility of SOC 2 means it also works well to combine with other standards, like HIPAA, GDPR, CPS 234, and Consumer Data Right, to name a few.
4. Attestation vs. Certification
SOC 2 is an attestation report, which provides a "System Description" of the business processes and control practices. ISO 27001 is a certificate confirming compliance. The System Description provides additional transparency and verified information to end users as it relates to your specific business, services and environment. That generally enables reduced security due diligence questions accordingly as those questions of enterprise customers are answered in the description, in a consistent format between organisations, and with verification. It also includes responsibilities as they relate to your third-party service providers, and the customer themselves as a user of your service to help vendor risk teams understand these dependencies.
Those high-level differences are the main things you should consider when determining which standard is right for you, although many organisations initially or eventually comply with both standards to cover their broader customer expectations. The more technical/detailed view comparing the two standards is as follows, including practitioner opinions that are more subjective at the end of the table.
| SOC 2 | ISO 27001 | |
| Governing Body | American Institute of Certified Public Accountants (AICPA) | Accreditation Bodies: North America - ANAB ANZ - JAS-ANZ |
| Origination | USA | UK |
| Assessor Requirements | Certified Public Accountant (CPA) | (Accredited) Certification Body |
| Structure | Principles and Criteria | Information Security Framework |
| Scope | The Services Provided to End Users; Includes Infrastructure, Software, Data, People & Procedures Relevant to those Services | The Information Security Management System (ISMS) |
| Focus | Controls to meet Trust Services Criteria based on design (Type 1) and operation (Type 2) | Policy and Processes to establish, implement, maintain and improve an ISMS based on design only |
| Assurance Coverage | Security; Optionally includes Availability, Privacy, Confidentiality & Processing Integrity | Information Security Only |
| Assurance Approach | Flexible; The Service Organisation (you) decides on the attestation audits to report on control design (Type 1) and operating effectiveness (Type 2) for a chosen date or period of time. This is usually influenced by the end user requesting the SOC 2 report(s) | Pre-defined; An initial certification is followed by a 3-year period of surveillance audits to maintain the certification |
| Period | Point in time or period of time | Point in time testing during a certification period |
| Deliverable | A Report including the System Description, controls to meet the Trust Services Criteria, tests performed by the auditor (Type 2 only) and the auditor and service organisation attestations. | A 1-page certification document confirming the organisation has met the requirements for certification. |
| Practitioner Opinions | SOC 2 provides a higher level of assurance by confirming the operating effectiveness of controls over a period of time. | ISO 27001 is designed for best practice, in contrast to SOC 2 which follows generally accepted practices. |
| SOC 2 is more relevant to customers as its scope is focused on the systems and services provided to those customers. | ISO 27001 certification is harder to achieve than a SOC 2 Report. | |
| There’s a higher level of quality in the SOC review process as it requires a CPA certified firm completing the assessment. | ISO 27001 audits are exhausting from all the face-to-face time. | |
| The flexibility with SOC 2 Scope, timing and approach can limit the assurance provided to customers. |
Which is More Suitable to You?
Both standards are intended to provide assurance to your customers. There’s three main considerations for what will best satisfy your customers:
-
Have your customer(s) specifically requested or mandated one of the two standards?
-
What locations are your customers based?
-
What industries do your customers operate in?
Customers prefer the standard they are more familiar with. European customers tend to prefer ISO 27001, whereas SOC 2 is preferred in the US. The more regulated Financial Services and Healthcare industries generally prefer SOC 2, while less regulated industries and government agencies generally prefer ISO 27001.
In Australia, there's a large network of ISO 27001 consultants, which we see generally leads to a stronger narrative of support for ISO 27001. This can be dangerous as we see some clients surprised when an Australian or international enterprise then mandates SOC 2 saying ISO 27001 is not enough. It's always best to ask your customers. That way, there's no surprises and you can make an informed choice. The best way to manage the expectation of your key stakeholders as a global company, is to assume both standards will be required at some point. Doing them both together at the start can be a great way to cover all bases and achieve efficiencies from the overlap.
Book a Meeting with us if you want to discuss further, or jump right into our Readiness Assessment software below. In 60 minutes, this will complete a compliance assessment and guide you on what's required for both standards and any others you select (HIPAA, GDPR, Consumer Data Right).







