The four functions of security and compliance software
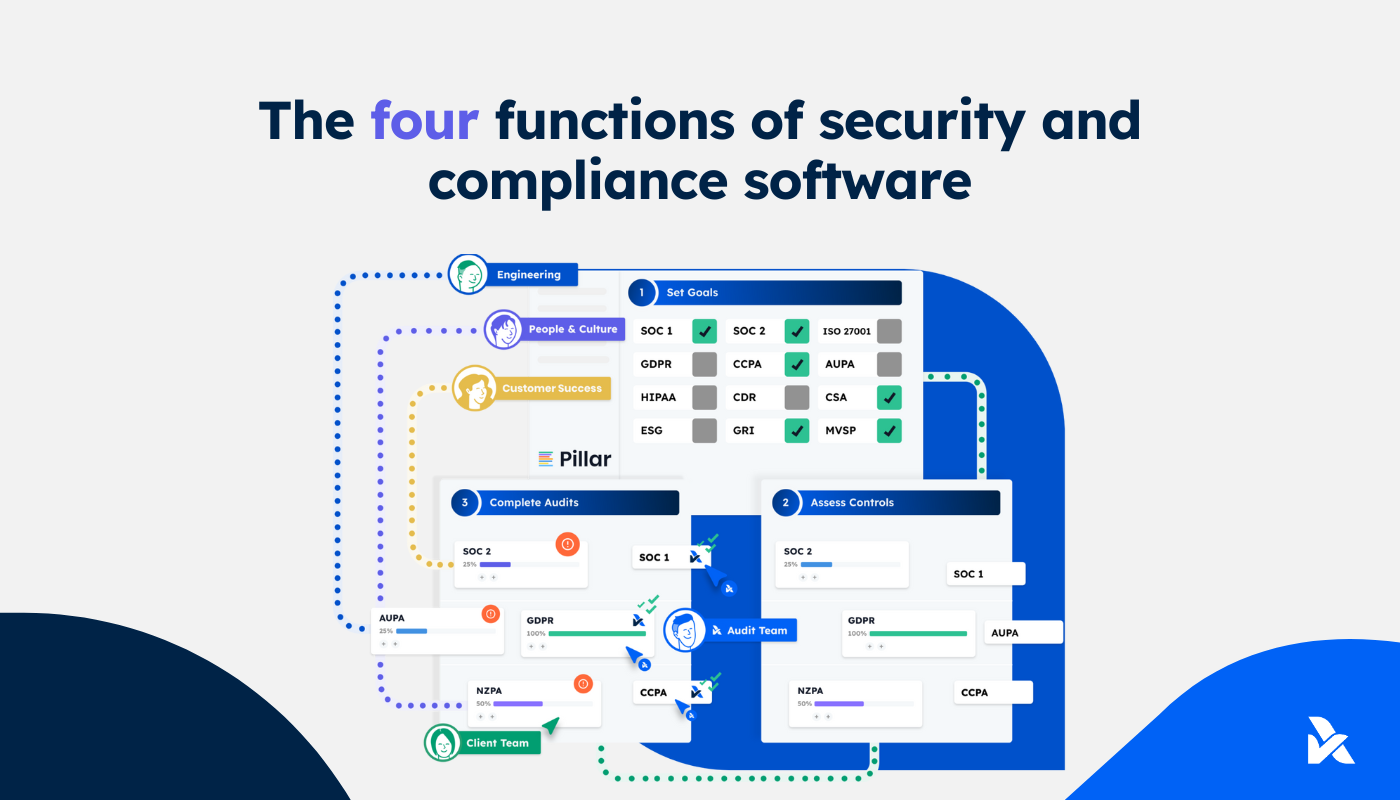
Security & Compliance software performs four powerful functions to assist you in achieving and maintaining your standards like SOC 1, SOC 2, and ISO 27001.
A game-changer in the information security and compliance industry has been the rise of software automation.
This disruption has been slower than in most other industries. In 2020, there's been a meteoric rise in the startups that have developed platforms and tools to automate, manage and simplify information security. That includes the automation of security practices and policies as well as the way those are documented and demonstrated to the auditors that provide SOC 1, SOC 2 and ISO 27001 certifications (among other standards).
We get a lot of questions about what these software solutions do, and whether it’s an alternative to our own Readiness Assessment software. To the contrary, we see it as a near-perfect complement. We have partnerships with the main platform providers; Vanta, Drata, Tugboat Logic, and Aptible Comply.
Our readiness software is a tailored assessment to identify your control activities and where there’s gaps. It prepares control descriptions for your SOC 2 report, and helps you prioritise your focus on control gaps requiring remediation. Due to our independence requirements as an audit services provider, we cannot design or implement your control activities. That's where these platforms perform a powerful function; with pre-built policies, functions to manage standard security practices, and integrations to monitor your infrastructure security settings.
Based on the same independence requirements, these platform providers cannot provide audit services. Their solutions are agnostic to the audit firm provider. The approach of audit firms varies significantly, so the platforms are designed to be a “one-size-fits-all” approach.
In short, these platforms simplify and automate the design and implementation of your controls. Ours simplifies and automates the way it applies to your business and how it's described in your SOC 2 report. Our software is free for our clients, and takes about an hour of your time. It’s almost a no-brainer to use it as a first step to clarify the path to compliance and where you can use those platforms to design and implement control activities to plug any gaps.
If you’re considering whether those platforms are right for you, worth the cost, and want to know how it fits in to your other activities, there's four key functions they perform:
1. Security practices out-of-the-box
Security practices are broad in scope and vary by nature. In some cases the platforms automate components of those security practices, with the remainder requiring manual activities, inside or outside the platform. The pre-built security practices out-of-the-box include;
- Policy templates
- Onboarding and off-boarding checklists
- Personnel and device tracking
- Risk assessments
- Third-party vendor register
- Vulnerability scanning and anti-virus
- Access control procedures and tracking
- Monitoring security configurations and review tasks
2. Compliance assessment and monitoring
Platforms like Vanta started with a security focus first, then incorporated functionality to map those security practices to standards like SOC 1, SOC 2 and ISO 27001. Since it's up to the auditor to determine and verify your compliance, the platforms assess generally accepted good practices and monitor the implementation of those practices. That's intended to cover most of what's required, and in some cases covers more than what's required so that it can be broadly applicable to varying firms approaches. The compliance assessment and monitoring is designed to provide a baseline, from which you can build on when dealing with the auditors as required.
3. Document management
There are two key value propositions of these platforms; assisting users in (1) achieving compliance, and (2) maintaining compliance. The document management functionality solves the latter by keeping 'all' audit documentation in one place. It's not feasible to have the whole organisations records in one platform; but the impressive integrations enable coverage of most of what's relevant to your InfoSec compliance. That includes integrations with leading cloud infrastructure providers to verify your key security configurations, and development tools like Github and JIRA to provide oversight of change and incident management practices.
4. Project management
Project management features aren't included in all the platforms. In those that do incorporate it, auditors can upload a request list for you to provide responses to. This allows you to see the progress, status and any areas requiring further evidence or responses from you. Similar to the value propositions above, this helps 'keep it all in one place' to manage your InfoSec compliance.
These information security compliance platforms like Vanta, Tugboat Logic and Aptible Comply have made their mark on the industry. On one hand, they've simplified, accelerated and reduced the costs of achieving InfoSec standards like SOC 1, SOC 2 and ISO 27001. The downside is the costs and in the context of a one-size-fits-all approach that may not fit with your existing practices or replace what's otherwise already been implemented in a manual or other way. It's worth exploring whether these platforms are right for you, as information security compliance is a marathon, not a sprint. The platforms may prove highly valuable to your business.







